How To Export LAPS Passwords from Active Directory with Powershell
In this guide, I’m going to show you how to export the LAPS passwords from Active Directory using a 3-line Powershell script.
This script automatically exports all LAPS passwords from Active Directory to a CSV file with the date appended to the file name. I then schedule this to run monthly using Task Scheduler.
Why export LAPS passwords?
I’m assuming if you ended up on this post, you know that LAPS is Microsoft’s way of automating password changes for local administrator accounts. I’ve been using LAPS for years, and it just works. Here’s a decent LAPS install guide if you haven’t set up LAPS yet.
So, why export LAPS passwords to begin with?
There are several reasons why you should to export them. Over the years, there have been 3 scenarios in which I wish I would’ve have an export of LAPS passwords:
- When moving Administrator users to Standard users. The user takes the laptop offsite, and the LAPS password has expired. I wish I would’ve had a way to look up what the previous password was when troubleshooting random issues or installing new software.
- DNS not resolving over the VPN. Occasionally, certain users won’t be able to get DNS to resolve over our OpenVPN Duo connection. This means that even though LAPS changes the password in Active Directory, their computer still has the old passwords. This means any admin-related tasks I need to do won’t work until they come back onsite.
- Domain controller unavailable. Although rare, there have been a few occasions where our domain was temporarily unavailable. While I could log in with Windows cached credentials on most machines, there were several servers I hadn’t logged into in a while and could not. Without being able to RDP to a domain controller, or launch the LAPS Fat Client UI, I had no way of accessing those machines.
If have any concerns about running into any of those scenarios above, then you might consider exporting LAPS passwords in case of emergency as well.
Isn’t exporting passwords a security concern?
Technically, yes. However, in my opinion, you have to weigh the risk vs potential reward. Sure, exporting passwords in plaintext and leaving them on your desktop isn’t secure. But if you’re exporting them monthly, storing them on your non-domain password vault, or into a file share locked down with tight ACL’s, then the risk is mitigated much more.
Also something to keep in mind, if you’ve granted your daily driver user account to view LAPS passwords and has permission to use the ADUC widget, then you can view all LAPS passwords right from your work PC anyway, without logging into a Domain Controller.
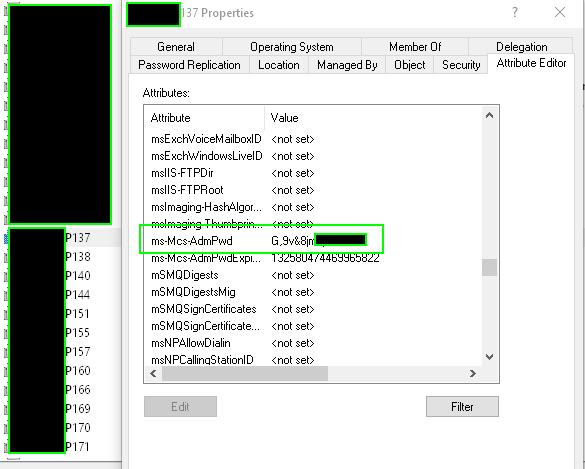
Open Active Directory Users & Computers > Right click a computer object > Properties > Attribute Editor. Scroll until you see the ms-Mcs-AdmPwd. You’ll see the LAPS password clear as day there.
Laps Export Powershell Script
This script assumes that LAPS has already been configured into your environment & that your user account already has access to view LAPS passwords using the Fat Client UI or from Active Directory Users & Computers.
This script loads the Active Directory module, finds the LAPS password fields, and then saves them to a CSV with the date appended to the file name. The only thing you’d need to change is the file path.
Just Open Powershell and paste this script:
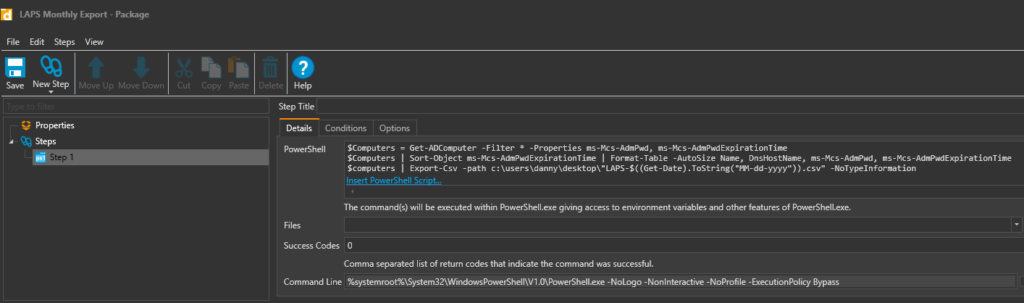
$Computers = Get-ADComputer -Filter * -Properties ms-Mcs-AdmPwd, ms-Mcs-AdmPwdExpirationTime
$Computers | Sort-Object ms-Mcs-AdmPwdExpirationTime | Format-Table -AutoSize Name, DnsHostName, ms-Mcs-AdmPwd, ms-Mcs-AdmPwdExpirationTime
$computers | Export-Csv -path c:\users\danny\desktop\"LAPS-$((Get-Date).ToString("MM-dd-yyyy")).csv" -NoTypeInformation
Then, save it to the location of your choice. For this example, I’m saving to C:\Scripts\LAPSexport.ps1.
Then, run the script to verify it works correctly. If it does, you should automate this procedure by creating a Scheduled Task.
LAPS Export Scheduled Task / PDQ Schedule
To schedule this to run on a schedule, open Task Scheduler > Create Task. Give it a name and configure the correct operating system version and user to run as.
- Under Triggers, select your frequency.
- Under Actions, choose Start A Program.
- Program Script: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
- Add Arguments: path to file (C:\users\Scripts\LAPSexport.ps1)
Then, just click OK and save. Right click and run the task to confirm that it’s working correctly.
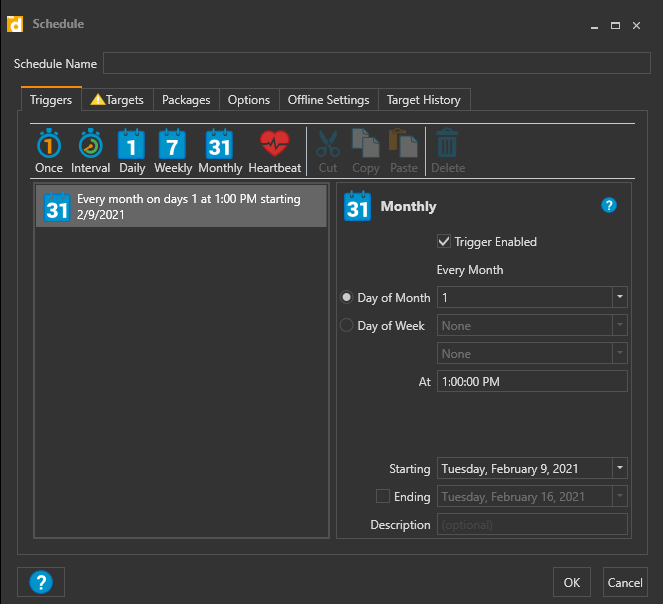
If you have PDQ Deploy in your environment, you could also schedule this to run monthly there.
- Create a new package. Give it a name like LAPS Monthly Export and paste the script in and SAVE.
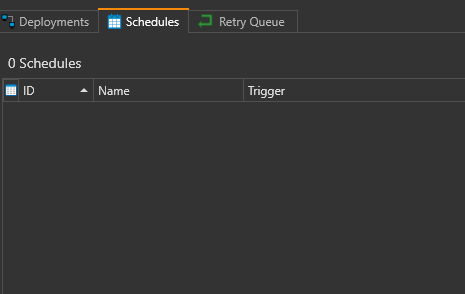
- Click the Schedules tab, then right click the empty space > New Schedule. Set the schedule.
- Click the Target tab, choose a PC that has access to view LAPS passwords, like your own.
Wrapping Up
Hopefully this simple script helps you export your LAPS passwords quickly and easily. Let me know if you run into any issues or have any modifications that you’ve made to the script.
My Homelab Equipment
Here is some of the gear I use in my Homelab. I highly recommend each of them.
- Server 2019 w/ Hyper-V
- Case: Fractal Design Node 804
- Graphics Card: NVIDEA Quadro K600
- CPU: AMD Ryzen 7 2700
The full list of server components I use can be found on my Equipment List page.