How To Limit Bandwidth in PfSense
Are you a PfSense user? Interested in setting up a firewall rule to "limit" the amount of bandwidth each device can upload/download? If so, then you are in luck! In this step-by-step guide, I'll show you how to use the Traffic Shaper wizard to create bandwidth restrictions on a per-device or per-network basis. And if you need to exclude some IP addresses from the rule, I'll show you how to do that as well.
Why Limit Bandwith in Pfsense?
Chances are that if you found this guide, you've already found a business case for limiting bandwidth per device. In an office or home environment, you may want to limit bandwidth to:
- Prevent 1 device from "pulling" too much bandwidth & saturating your network
- Manage bandwidth on a per-device or per-network basis. (I.e. - IoT VLAN gets 50mbps, but DHCP devices get 100mbps)
- Create bandwidth schedules (i.e - only apply restrictions during business hours, but stop applying after hours when server backups are running)
- Improve VOIP phone call clarity.
The last one was especially true in my corporate network. Although I have QoS traffic shaping rules already setup on our VPN interface, the rules only seem to apply on phones physically connected at HQ. I haven't been able to get the QoS rules to apply on VPN-connected phones. This means that if a user starts downloading a large file, any VPN-connected phone will experience choppiness, resulting in complaints and a bad experience for customers on the other line.
I could probably get the QoS rule fixed to fix our main issue, but at the end of the day - our employees don't really NEED the ability to max our our available bandwidth. Sure, file downloads will take a little longer than employees are used to. But the advantages far outweigh the disadvantages in my book.
How To Create Traffic Shaper Rules
Log into your PfSense firewall by IP address. The default IP address is 192.168.1.1, but since I'm on a different scope mine is 172.16.0.1:
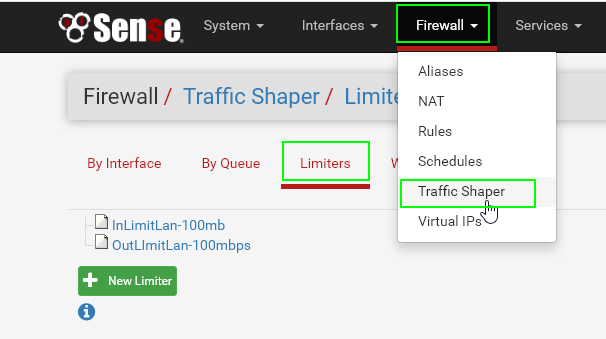
Step 1: Navigate to Traffic Shaper tab
Click the Firewall tab > Traffic Shaper > Limiters tab.
Then, click New Limiter.
Step 2: Create Inbound & Outbound Limiters
Once you create both the inbound and outbound limiter rules, you will apply these limiters to firewall rules on the LAN interface.
You can create the two limiters below without rebooting the Pfsense firewall. The limiters won't go into effect until you create a new firewall rule and target a certain IP address or range. For testing, I'll have you test the limiter with your computer's IP address first. If that test is successful, then you can either target a network range or group of IP addresses (using an IP alias).
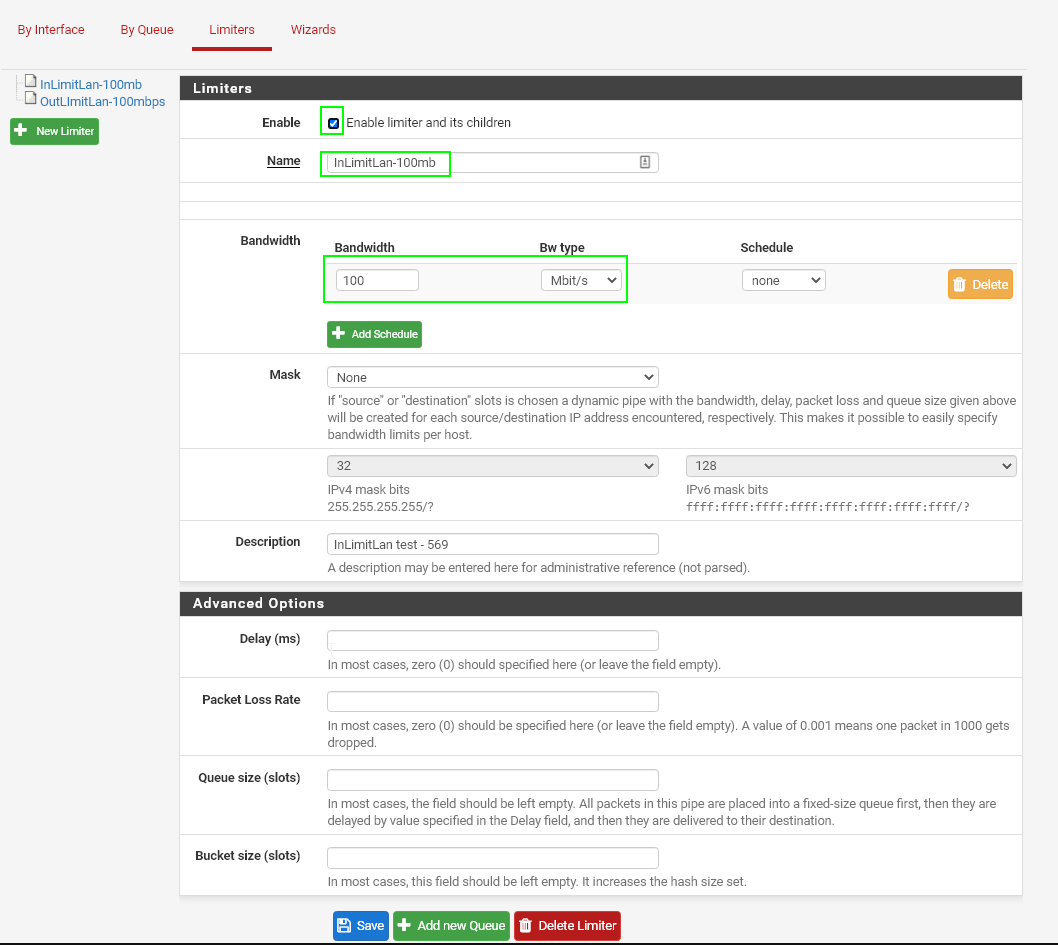
Inbound Limiter
Create a Limiter like the screenshot below.
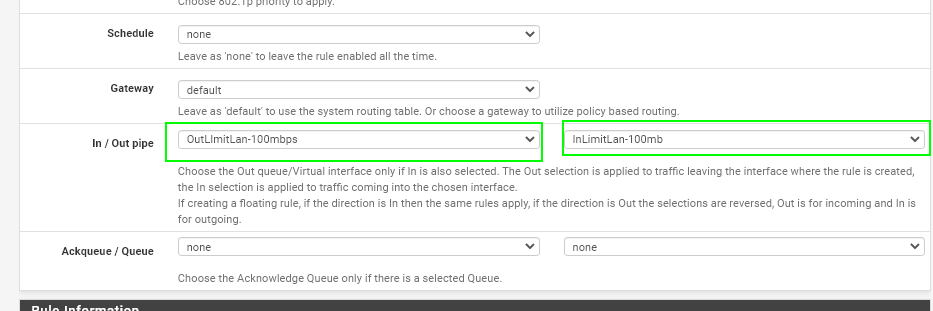
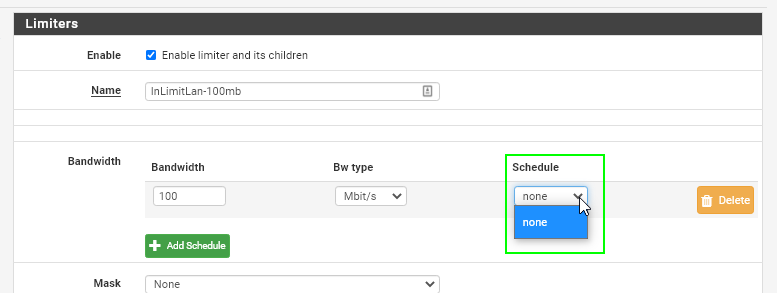
Check the box for "Enable limiter and its children", give your limiter a useful name (InLimitLan-100mbps), and then specify what you want your upper threshold bandwidth to be.
Then, click save. Your Inbound limiter has now been completed.
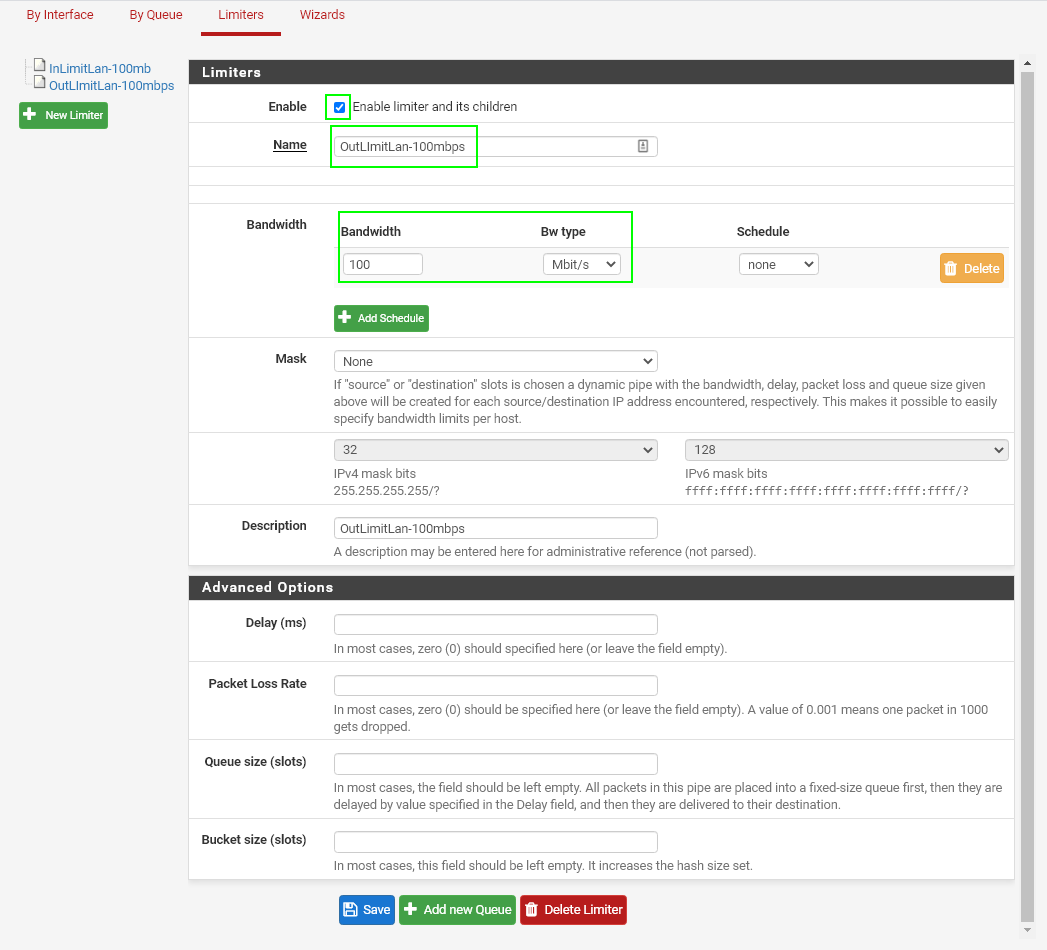
Outbound Limiter
Create a Limiter like the screenshot below. Once you create the firewall rule, you will
Check the box for "Enable limiter and its children", give your limiter a useful name (OutLimitLan-100mbps), and then specify what you want your upper threshold bandwidth to be.
Step 3: Create LAN Firewall Rule
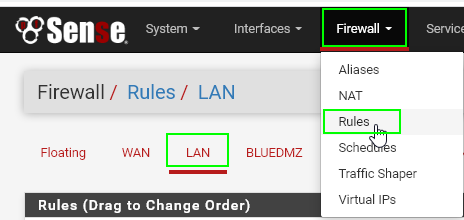
Now that the limiters are created, it's time to create a firewall rule on the LAN interface used specifically for limitating bandwidth.
Navigate to Firewall > Rules > LAN tab.
Scroll to the bottom and create a new rule. Make sure to select the UP arrow so the rule gets placed at the very top. Reminder: placement of firewall rules matter as they processed from top to bottom. Since we want this rule applied before all other rules, we want this rule at the top.
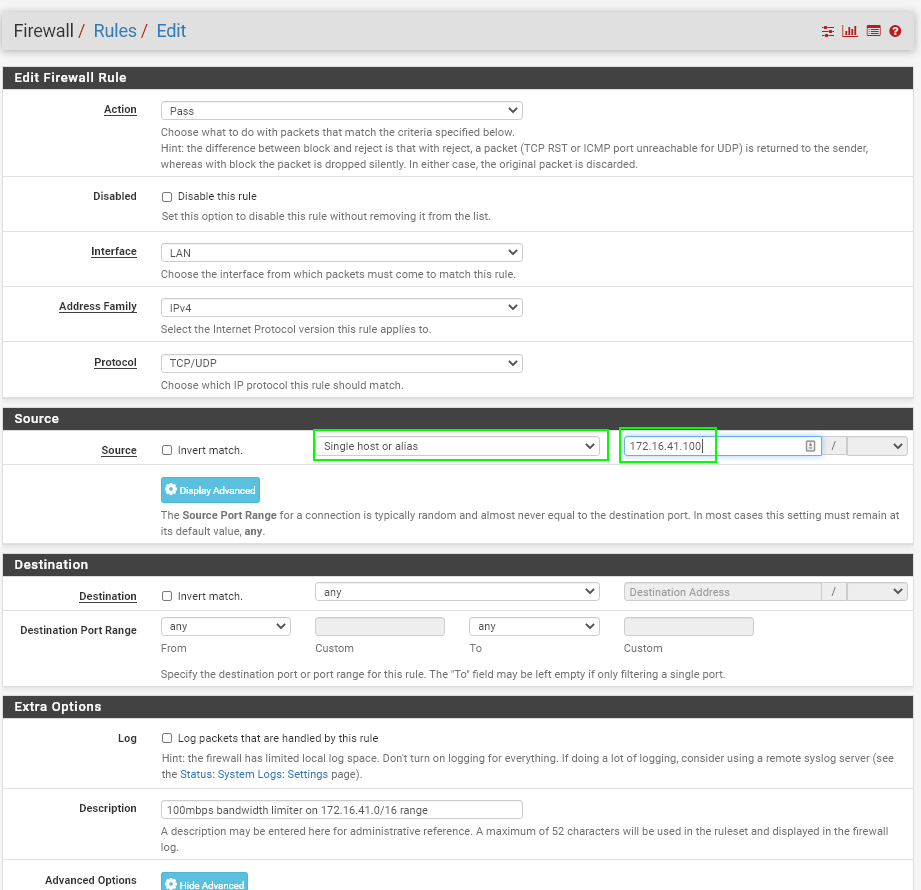
Create your rule exactly like mine, except change the IP address in the SOURCE section to your computers IP address:
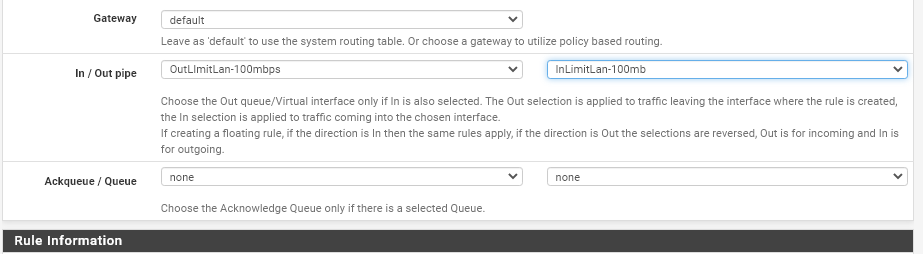
On the Extra Options section, click Display Advanced. A new "Advanced Options" panel will show up.
Scroll to the bottom and locate the In/Out Pipe section. Your inbound (download limiter) goes in the second spot. Your outbound (upload limiter) goes in the first. If you've been following along, just add yours exactly as I did.
If you're ready to test, click SAVE. The rule will apply immedietely. No need to reboot your PC, the firewall, or release/renew.
Step 4: Testing & Tweaking the Rule
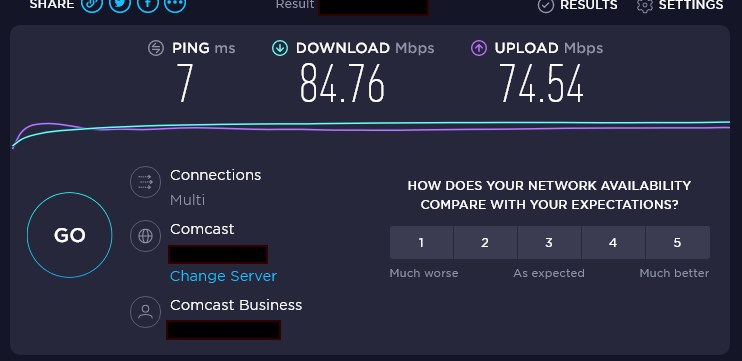
Next, test your rule by going to https://speedtest.net. If all goes well, your computer should never hit the upper limit you configured. Mine was set to to 100mbps, so as you can see it is applying correctly:
Keep in mind, just because you've set a hard limit of 100mbps, that doesn't mean you are going to hit 100mbps for every file download. It just means you are only allowed to use bandwidth UP TO 100mbps, which could be much lower.
Setting Limiter for Network Range
Obviously, in large networks, adding individual IP addresses is going to be a pain. So, you can target specific IP address ranges instead!
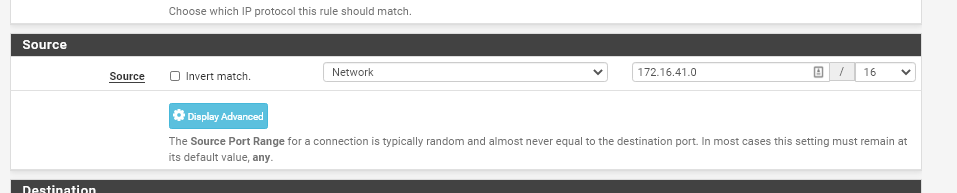
If this is something you want to set up, in Step 3 you would change from "Single Host or Alias" to "Network". Then, just add the network. My example below will target all DHCP devices in the 172.16.41.x range.
Setting Limiter for Groups of Computers/IP address
Let's say you don't want to limit the bandwidth consuption on an entire network range. Instead, you can target a group of IP addresses. For example, all of my servers are in the same IP address range. I don't necessarily want to place the same limiter on ALL servers, just a few.
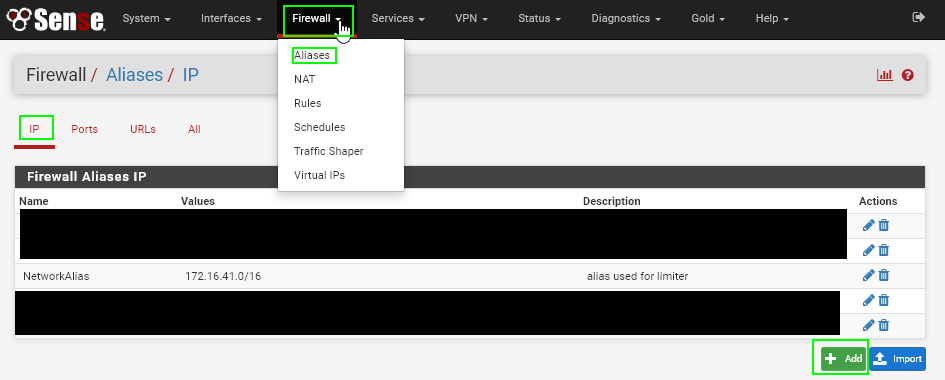
To set this up, we use IP Aliases. Navigate to the Firewall > Aliases > IP tab. Then, click the Add button.
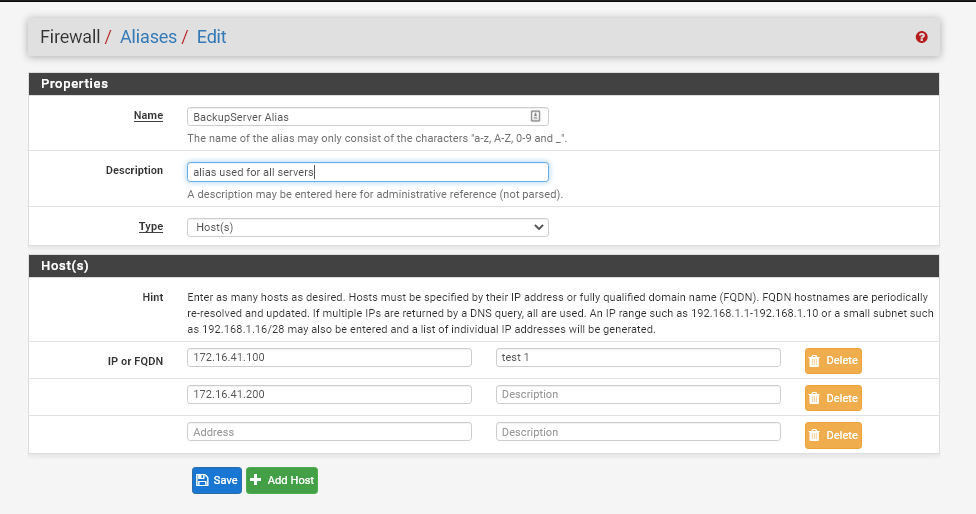
Choose type "Host" and then add as many IP addresses as you want. Click Save once complete.
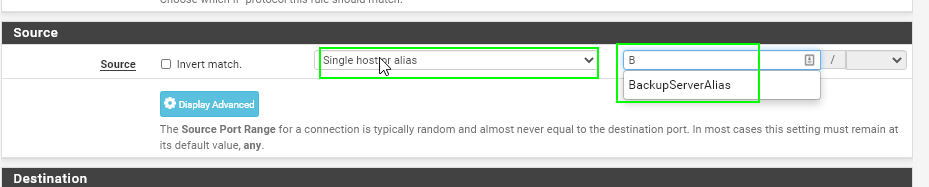
Next, navigate back to the new firewall rule you created. Edit the Source to Single Host or Alias and then start typing your alias name.
That's it! You can now target a group of IP addresses, either from the same range or different, with the same rule.
Creating IP Exclusions for Traffic Limiting
I haven't figured out a better way to do this, but the best way to exclude an IP address from the limiter is to give it an IP address outside of the scope. For example, if you've created 3 firewall rules for IP ranges 172.16.41.0/16, 172.16.42.0/16, and 172.16.43.0/16, you would give the computer or server an IP address like 172.16.45.1.
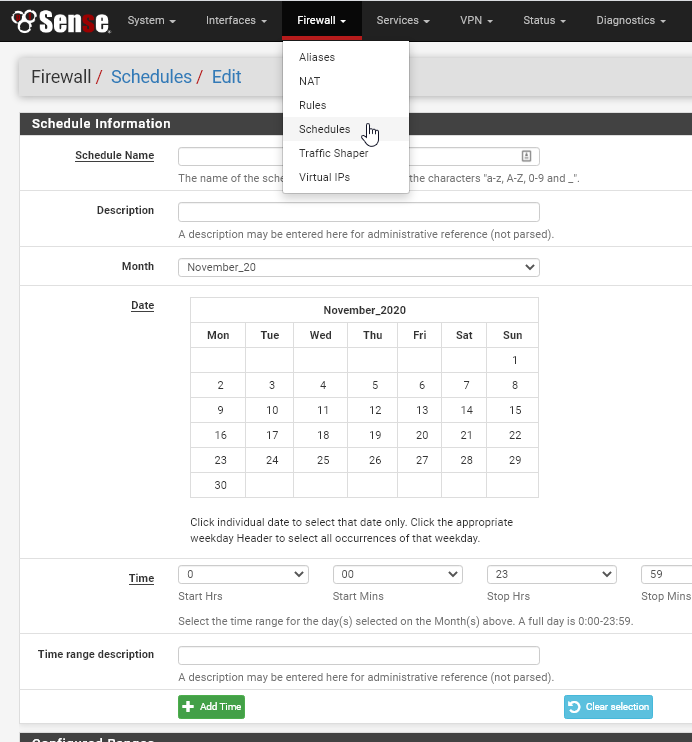
Creating Traffic Limiting Schedules
You may have noticed the "Schedules" tab under the Limiters section. Here's an example usecase: Create a schedule if you want to limit bandwidth during business hours, but keep it wide open after hours for backup purposes.
If you don't have a schedule set, this will show none in the limiter.
To set a schedule. you would go the Firewall > Schedules section:
Wrapping Up
That's it! This is something I've been wanting to implement for a while, but honestly I thought it would be more difficult to setup. Hopefully it helps you set things up as well! If you do run into any issues with the setup, just disable the firewall rule while you keep testing.