Chrome Extension Checker for PDQ Deploy
In this guide, I'm going to show you how to create a PDQ Deploy sequence to check whether or not a computer has a certain Google Chrome extension installed. All the other scripts I could find show every single extension a user has installed, which isn't helpful when hunting down maliciously installed extensions.
In my case, I needed to find the malicious extension Auto Refresh because it was serving adult ads to our users.
https://ir-na.amazon-adsystem.com/e/ir?t=smarthomepursuits-20&l=li3&o=1&a=B079MFTYMVThe script works by checking for the path of the extension. If it finds the path, it outputs a file to their users computer appended with their computer name, which then gets copied to a network share.
There's probably a much better way to accomplish this, so I welcome all updates/recommendations. I wrote this very quickly today in order to find and get rid of it as quickly as I could.
As you can imagine, Chrome extensions GPO's are getting pushed up on my todo list.
Prerequisite Notes
All Google Chrome Extensions are installed here:
**Other than Google-specific extensions like Google Keep.
C:\users\USERNAME\appdata\local\Google\Chrome\User Data\Default\extensions\To find a Chrome extension ID
For this script to work, you need to know the extension ID (as the folder that gets created after installing the extension has the same name).
To find the ID, open Chrome > Click the 3 dots > More Tools > Enable Developer Mode. The ID will then be displayed for each app.
You'll need to know this when checking for legitimate extensions during testing.
Create a New PDQ Deploy Package
Create a new PDQ Deploy package and name it Chrome Extension Checker.
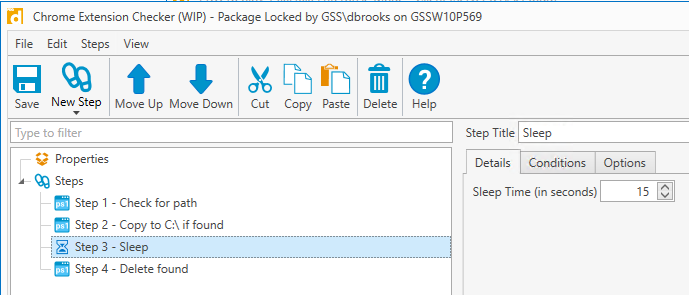
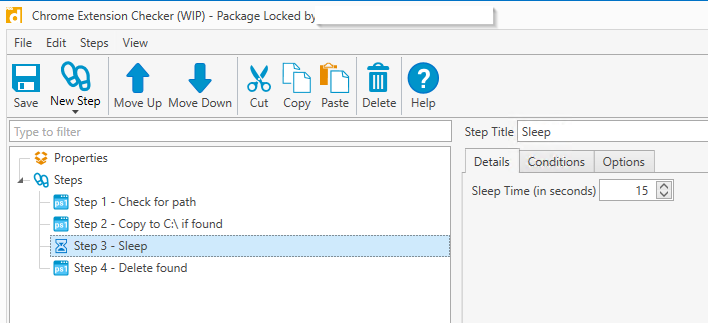
Add 4 steps exactly as below. You will only need to change the extension ID and paths.
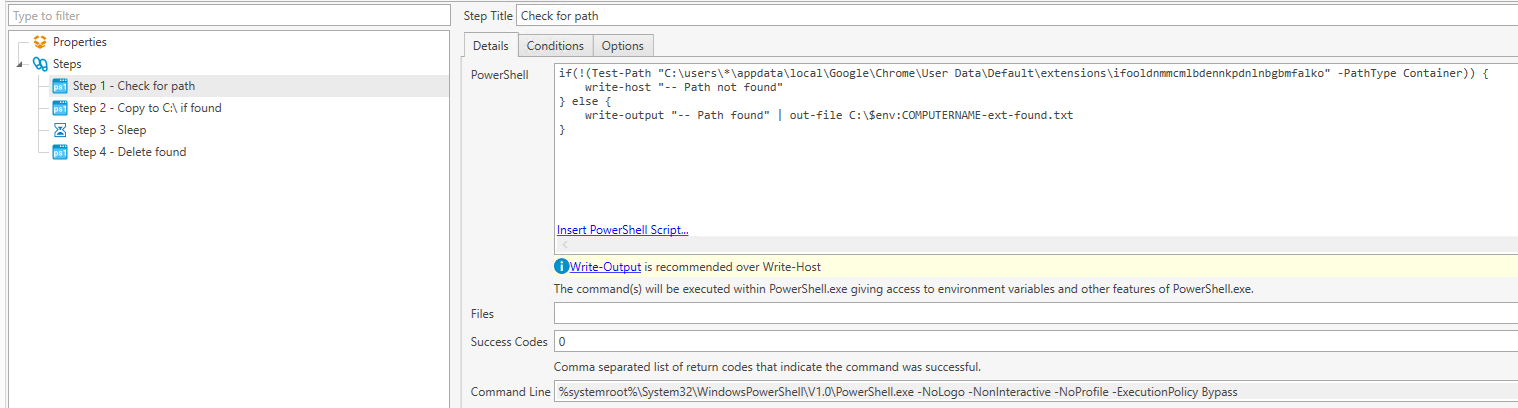
Step 1: Check for path
This step checks for the file path of the extension. If it finds the path, it creates a small text file appended with the computer name and adds it to C:\ drive. A file is not created if the extension is not found.
Bonus: This checks for the extension installed under ANY user profile.
The extension ID below is for the malicious Chrome extension Auto Refresher, which we found on 6/10/2020. If looking for other extensions, replace the ID.
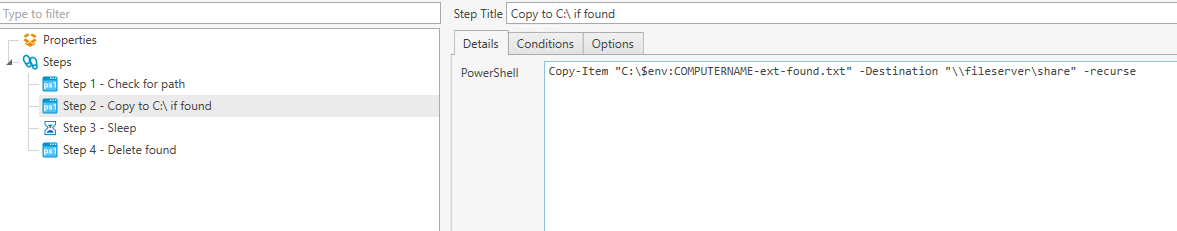
if(!(Test-Path "C:\users\*\appdata\local\Google\Chrome\User Data\Default\extensions\ifooldnmmcmlbdennkpdnlnbgbmfalko" -PathType Container)) { write-host "-- Path not found" } else { write-output "-- Path found" | out-file C:\$env:COMPUTERNAME-ext-found.txt }Step 2: Copy to Network Drive
This step copies the file that was just created to a network share.
Copy-Item "C:\$env:COMPUTERNAME-ext-found.txt" -Destination "\\fileserver\share" -recurseStep 3: Sleep
This step is probably not necessary, but I added a 15 second sleep/ wait timer just in case it took longer on some computers.
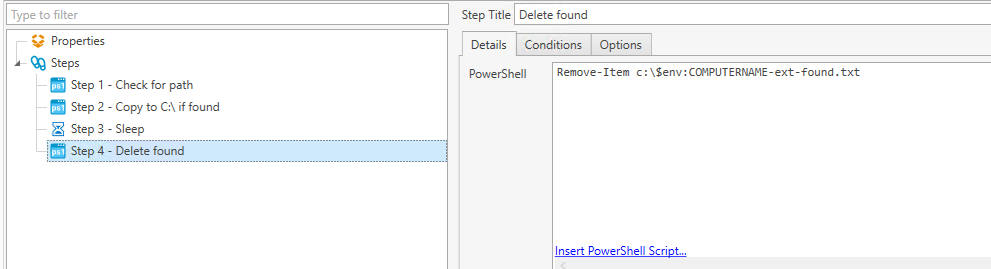
Step 4: Delete File
This final step deletes the text file created in step 1.
Remove-Item c:\$env:COMPUTERNAME-ext-found.txtFinal Step: Edit All 4 Steps to Continue After Error
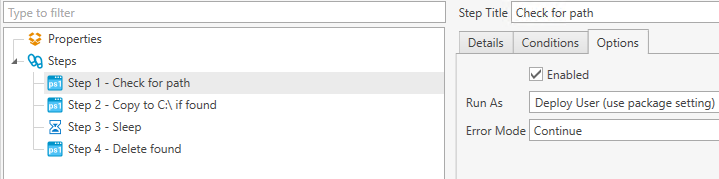
For Steps 1-4, go to the Options tab, and change the Error Mode to Continue. Otherwise it will fail on computers that do not have the path.
Running the Chrome Extension Checker
After the package is complete, right click the package, Deploy Once, and choose your collection.
I recommend editing the ID in Step 1 with a KNOWN GOOD ID or against a small test group before running against the company. (For example, I used the Honey extension)
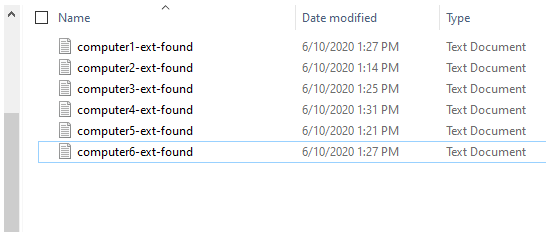
After the script completes, you should see a list of computer names in your network share like this:
Cleaning up and Removing the Extension
Now that you have the list of computers that have the Auto Refresh extension, you have a few options.
- Option 1: (Recommended) Log in with the user and remove it through Chrome
- Option 2: If you are using LAPS and/or know the local administrator password, you can browse to the extensions folder path via this path:
\\Computer1\c$\Users\USERNAME\AppData\Local\Google\Chrome\User Data\Default\ExtensionsWe ran several different AV scans such as Carbon Black and Malwarebytes, and there was nothing lingering after uninstalling. Chrome worked perfectly as soon as we removed it.
Locate the folder, and click delete. If the folder does not exist, check another user profile.
I prefer option 1 because Option 2 still shows the extension in Chrome, even though all the necessary files have been deleted.
Wrapping Up
If this script was useful, let me know know in the comments below! I plan on cleaning this script up and adding the ability to delete the folder to the script in the future.
Let me know if you have any recommendations for improving it or making it simpler.